Ripple's Chief Technology Officer alerts users about a compromised xrpl.js package that could potentially steal private keys from XRP wallets through malicious code in recent versions of the XRPL developer library.
XRP Developer Library Compromised with Key-Stealing Code
David Schwartz, chief technology officer at Ripple, has issued an urgent warning on social media regarding malicious code discovered in recent versions of the library for XRPL developers. This compromised code poses a serious threat as it could potentially steal users' private keys, putting their XRP holdings at risk.
The security issue was first identified by Aikido Security, which revealed that the XRPL package on NPM (the default package manager for JavaScript) had been compromised. Several new versions of xrpl.js, the software development kit for the XRP Ledger, were recently released, containing this malicious code. Security experts became suspicious when they noticed these code changes were not present in the official GitHub repository.
XRP Users Should Consider Affected Private Keys as Stolen
The malicious code was designed to secretly transmit private keys to an unknown domain, representing a significant security breach for anyone using the compromised versions of the software development kit. Aikido Security was able to identify this suspicious code change using their AI-powered threat monitoring system, potentially preventing more widespread damage.
Developers and users who inadvertently installed these compromised versions should immediately consider their private keys compromised and take appropriate security measures. This includes creating new wallets with fresh private keys and transferring any XRP funds to these secure wallets as soon as possible.
XRP Ledger Remains Secure Despite SDK Breach
It's important to note that regular XRP users who rely on established and well-known applications such as Xumm are highly unlikely to be affected by this security breach. The threat primarily impacts developers and services that directly implement the compromised versions of the xrpl.js library.
"XRPL is fine, it is in the developer SDK that was compromised, this is widely used by cryptocurrency applications and services but the ledger itself remains secure," Aikido Security clarified in their announcement. This assessment has been confirmed by Mayukha Vadari, senior software engineer at RippleX, providing reassurance that the core XRP Ledger infrastructure remains uncompromised.
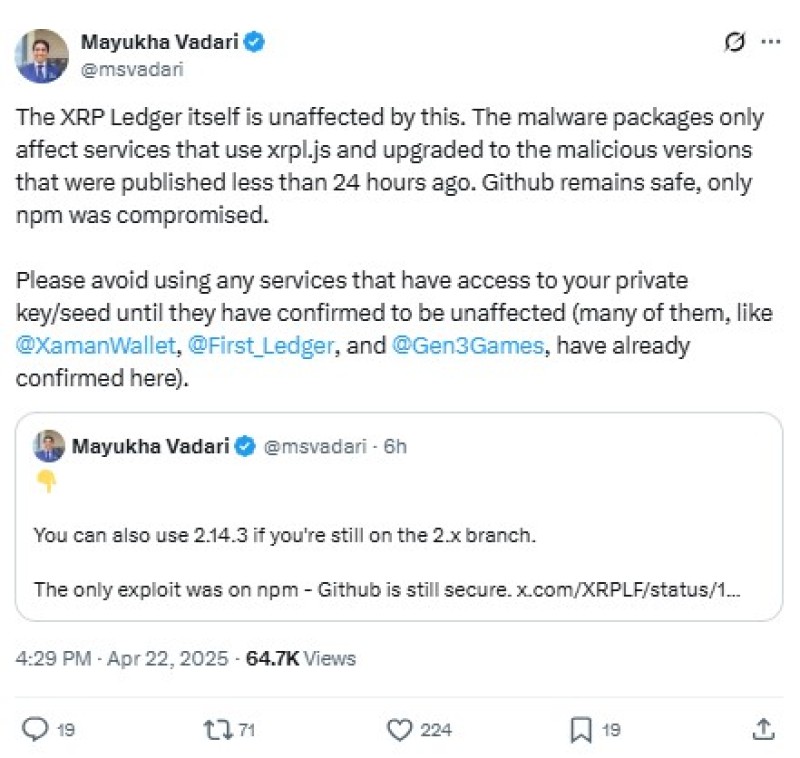
The XRP Ledger Foundation's official maintainers have already removed the malicious versions from the NPM repository, preventing further installations of the compromised software. The XRP Ledger itself continues to operate normally, with its underlying security architecture remaining intact.
XRP Security Firm Investigating Threat Actors
Aikido Security has stated that they are actively investigating the threat actors responsible for this attack. "We are investigating. We have some ideas on the threat actors involved, it fits a pattern we see a lot. Will update when we can confirm," the security firm noted in their announcement.
This type of supply chain attack represents a growing threat in the cryptocurrency ecosystem, where compromised development tools can potentially affect numerous downstream applications and services. The incident serves as an important reminder for XRP developers to verify the integrity of their dependencies and implement appropriate security measures to protect their users' assets.
For the broader XRP community, this incident highlights the importance of using trusted wallet solutions from reputable providers and regularly updating security practices. While the XRP Ledger itself remains secure, this compromise of developer tools demonstrates how attackers are increasingly targeting the ecosystem's infrastructure rather than attempting to breach the underlying blockchain technology directly.
 Saad Ullah
Saad Ullah

 Saad Ullah
Saad Ullah


